Data security: Matters
We prioritize the protection of your data, with robust compliance in place to ensure its safety.
Data encryption
Protects sensitive information and ensures data security during transfer and storage.
Zero-trust architecture
Enhances security by minimizing trust and ensuring verification at every access point.
GDPR Compliance
Essential for meeting global privacy standards and ensuring customer trust in handling data.
ISO Certifications
We protect your CRM data with globally recognized security and cloud standards.
Access control
Prevents unauthorized access by enforcing strict and customizable user-level permissions.
Pen testing
Regular security assessments to identify vulnerabilities and improve system defenses.
Independent audits
External validation of security practices ensures compliance and builds customer trust.
End-to-end data integrity
Guarantees consistency and reliability across its entire lifecycle, from input to output.
Secure data handling
Your data stays protected with encryption and industry-standard security.

Our Trust Center
Dedupely’s Trust Center, powered by Vanta, provides a centralized space where you can explore our commitment to security, compliance, and transparency.
Security documents
Stay updated with our latest articles and insights.



Pen testing

Dedupely conducts regular penetration testing to ensure our platform remains secure and reliable. These assessments are designed to strengthen security, protect CRM data, and adapt to evolving challenges.
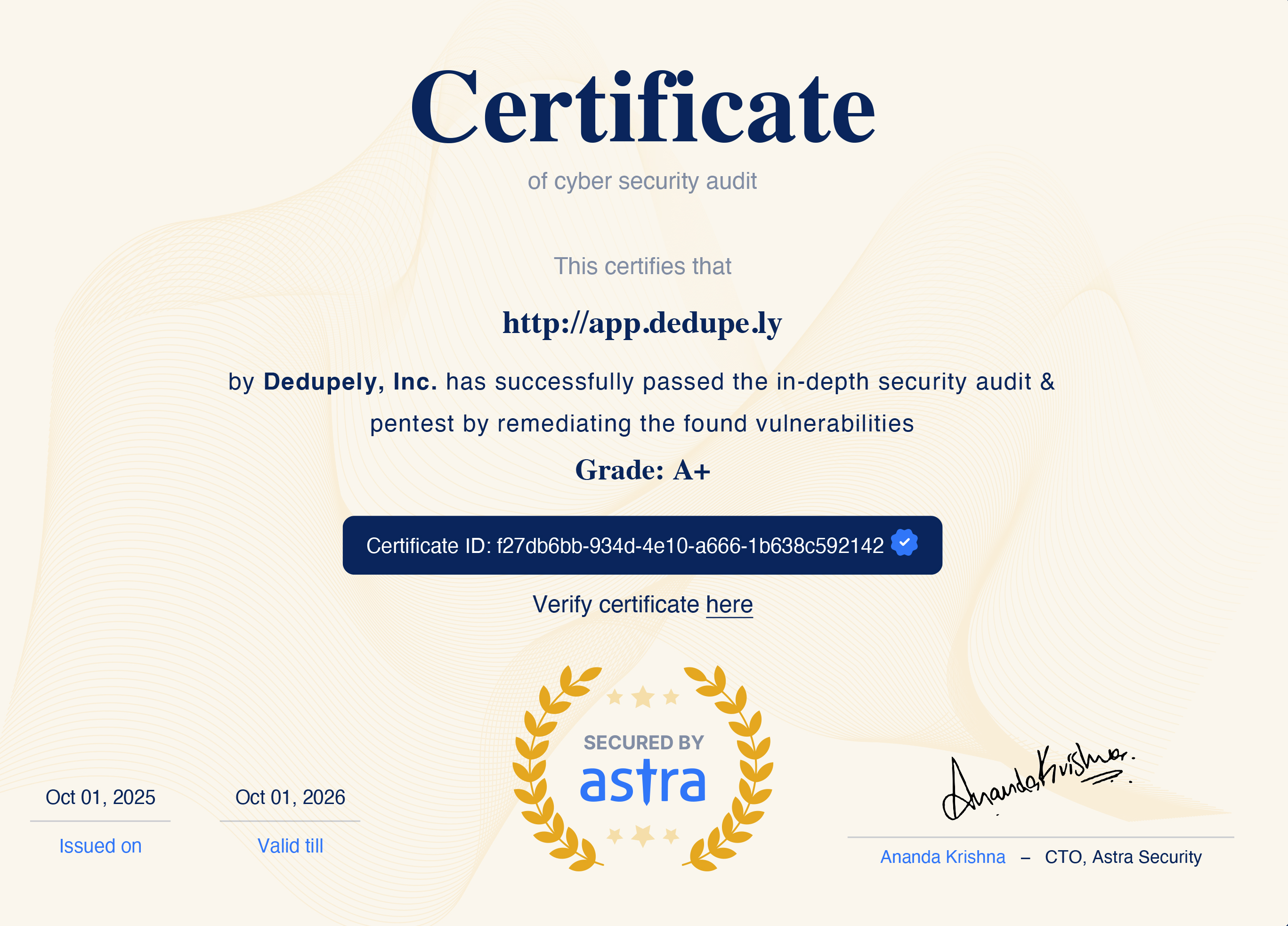

Regular security audits and independent reviews
Dedupely undergoes regular audits and external reviews to validate the effectiveness of our security measures. These evaluations confirm our compliance with industry standards and ensure transparency in how we handle your CRM data.
Security partners

From Astra cutting-edge penetration testing to Vanta compliance automation, BD Emerson expert audits, and Mastermind assurance services, each partner plays a crucial role in strengthening our platform and protecting your CRM data.

User permissions and least access control
We ensure that only authorized team members can access CRM data with flexible permissions and strict access controls. These tools are tailored to help you define roles, maintain boundaries, and protect sensitive information.
FAQs
Find answers to common questions about Dedupely, its features, and integration capabilities.
Your data remains private and secured. Dedupely ensures that no unauthorized users, including Dedupely employees, can access or modify your CRM records.
Dedupely’s algorithm includes built-in safeguards to prevent anomalies from affecting your data. However, you maintain full control over merge actions and should review results for accuracy.
Yes, Dedupely retains a cached copy of your data while you use the service. This allows us to continuously find and merge duplicates using the latest updates in your CRM.
Yes, you have full control over your data. You can delete it from Dedupely at any time.
Yes! Dedupely is ISO 27001:2022 certified, including ISO 27017 (Cloud Security) and ISO 27018 (Personal Data Privacy in the Cloud).
Dedupely partners with third-party services only to enhance performance, in full compliance with GDPR and ISO standards. Your data is never used for marketing or external sales.
We use OAuth authentication and rotate tokens continuously to ensure security. Permissions are carefully managed to prevent unnecessary access.
Dedupely offers Two-Factor Authentication (2FA), session timeouts, Google sign-in, and encrypted passwords. IP whitelisting is also available for extra security.
Yes, 2FA is available to add an extra layer of security.
Yes, you have full control over user roles and permissions. You can add, edit, and remove users as needed.
Yes! Dedupely maintains activity logs, tracking both merges and user actions for transparency.
Your data is processed in Google Cloud and AWS North Virginia (USA) regions.
Dedupely follows a structured Incident Response Plan compliant with ISO 27001, 27017, and 27018 standards. If a security breach occurs:
- Detection & reporting: Employees report incidents immediately, and severity is classified (P0–P3).
- Containment & mitigation: The Incident Response Team (IRT) assesses impact and executes rollback plans if necessary.
- Investigation & root cause analysis: Logs and evidence are reviewed to determine the cause and prevent recurrence.
- Communication & notification: Affected users, regulatory bodies, and internal executives are informed per legal requirements.
- Remediation & prevention: Vulnerabilities are patched, monitoring is enhanced, and preventative measures are implemented.
- Post-incident review: Findings are documented, and lessons learned are integrated into security practices.
- Compliance & audit: Incident responses are logged for audit and regulatory compliance.
15,000+ businesses
feel the magic